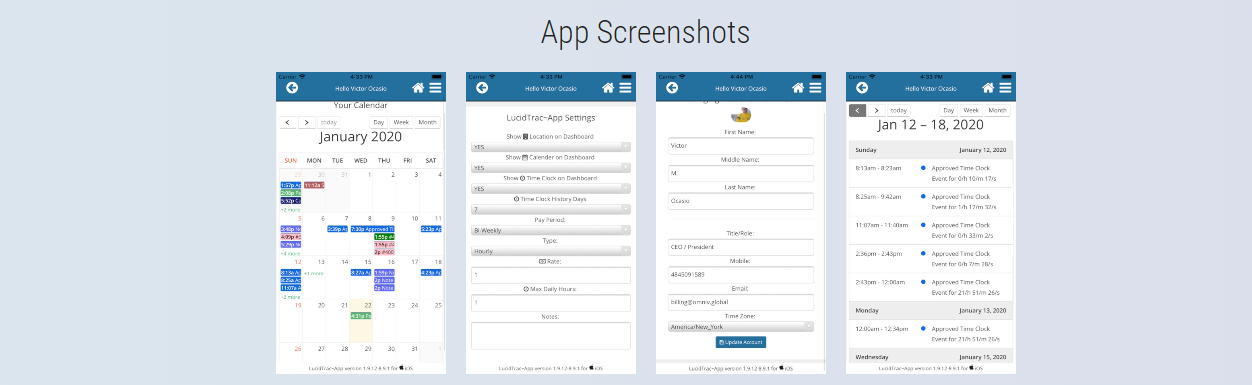
2025 Update: 7 Best Practices to Avoid Phishing Campaigns
As we dive into 2025, phishing campaigns continue to evolve and become more sophisticated. Cyber attackers are exploiting new technologies and tactics to deceive individuals and organizations, making it essential to stay vigilant and proactive in protecting yourself and your business. In this updated post, we'll discuss the latest phishing trends and provide 7 best practices to help you avoid falling victim to these malicious attacks.

New Phishing Campaigns to Watch Out For
-
AI-Powered Phishing: Attackers are leveraging artificial intelligence (AI) to create highly convincing phishing emails, messages, and even deepfake videos. These AI-generated attacks can mimic the tone, language, and style of legitimate communications, making them increasingly difficult to detect. For instance, AI-powered phishing emails can use natural language processing to craft messages that are almost indistinguishable from those sent by real people.
-
SMS and Messaging App Phishing: With the rise of mobile device usage, phishing campaigns are shifting from email to SMS and messaging apps like WhatsApp, Facebook Messenger, and Signal. Be cautious of suspicious messages or links sent via these platforms. Attackers are using these channels to trick victims into revealing sensitive information or installing malware on their devices.
-
Cloud Service Phishing: As more businesses move to the cloud, attackers are targeting cloud services like Google Drive, Dropbox, and Microsoft Azure. Be wary of phishing emails or messages asking you to sign in or provide sensitive information. Cloud service phishing can lead to unauthorized access to your cloud storage, compromising your data and potentially leading to financial losses.
-
Voice Phishing (Vishing): Attackers are using voice calls to trick victims into revealing sensitive information. Be cautious of unsolicited calls asking for personal or financial information. Vishing attacks often use social engineering tactics to build trust with the victim, making them more likely to divulge sensitive information.
The Anatomy of a Phishing Attack
To better understand how phishing attacks work, let's break down the typical steps involved:
-
Reconnaissance: Attackers gather information about their target, often using social media, online directories, or data breaches to collect email addresses, names, and other personal details.
-
Crafting the Phishing Email or Message: Attackers create a convincing email or message that appears to come from a legitimate source, such as a bank, social media platform, or online shopping site.
-
Sending the Phishing Email or Message: The attacker sends the phishing email or message to the target, often using spoofed email addresses or messaging apps to make it appear legitimate.
-
Victim Interaction: The victim receives the phishing email or message and interacts with it, either by clicking on a link, downloading an attachment, or providing sensitive information.
-
Malware Installation or Data Theft: If the victim interacts with the phishing email or message, the attacker can install malware on their device or steal sensitive information, such as login credentials or financial data.
7 Best Practices to Avoid Phishing Campaigns
-
Verify Sender Information: Always verify the sender's email address, phone number, or messaging app ID to ensure it's legitimate. Scammers often use spoofed or fake contact information.
-
Be Cautious of Urgent or Threatening Messages: Phishing campaigns often create a sense of urgency or fear to prompt you into taking action. Be wary of messages claiming your account will be suspended or that you'll face severe consequences if you don't respond immediately.
-
Use Two-Factor Authentication (2FA): Enable 2FA whenever possible to add an extra layer of security to your accounts. This can include SMS codes, authenticator apps, or biometric authentication.
-
Keep Software and Operating Systems Up-to-Date: Regularly update your software, operating system, and apps to ensure you have the latest security patches and features.
-
Use a Secure Email Gateway: Implement a secure email gateway to filter out phishing emails and spam. This can help reduce the risk of phishing attacks reaching your inbox.
-
Use Anti-Phishing Tools and Browser Extensions: Utilize anti-phishing tools and browser extensions like phishing detectors or ad blockers to help identify and block malicious content.
-
Regularly Back Up Your Data: Regular backups can help you recover in case you fall victim to a phishing attack or other types of cyber threats.
Additional Tips for Businesses
-
Conduct Regular Security Awareness Training: Educate your employees on the latest phishing tactics and best practices to avoid phishing attacks.
-
Implement a Incident Response Plan: Develop a plan to respond quickly and effectively in case of a phishing attack or other security incident.
-
Use Advanced Threat Protection: Implement advanced threat protection solutions, such as email security gateways and endpoint protection, to detect and block sophisticated phishing attacks.
Additional Tips for Businesses
-
Conduct Regular Security Awareness Training: Educate your employees on the latest phishing tactics and best practices to avoid phishing attacks.
-
Implement a Incident Response Plan: Develop a plan to respond quickly and effectively in case of a phishing attack or other security incident.
-
Use Advanced Threat Protection: Implement advanced threat protection solutions, such as email security gateways and endpoint protection, to detect and block sophisticated phishing attacks.
Staying Ahead of Phishing Campaigns
As phishing campaigns continue to evolve, it's essential to stay informed and adapt your security practices accordingly. By following these 7 best practices and staying vigilant, you can significantly reduce the risk of falling victim to phishing attacks. Remember to always be cautious when interacting with emails, messages, or links from unknown sources, and never provide sensitive information without verifying the authenticity of the request.
2025 Trends to Watch
As we move into 2025, several trends are emerging that could impact the phishing landscape:
-
Increased Use of AI and Machine Learning: Attackers are likely to continue leveraging AI and machine learning to create more sophisticated phishing attacks.
-
Growing Focus on Cloud Security: As more businesses move to the cloud, attackers will increasingly target cloud services and infrastructure.
-
Rise of Voice Phishing: Voice phishing, or vishing, is becoming a growing concern as attackers use voice calls to trick victims into revealing sensitive information.
-
Expansion of Phishing Attacks Beyond Email: Phishing attacks are no longer limited to email; attackers are using messaging apps, social media, and other channels to target victims.
What to Expect from Phishing Campaigns in 2025
Based on current trends and emerging threats, here are some predictions for what we can expect from phishing campaigns in 2025:
-
More Sophisticated Attacks: Phishing attacks will continue to become more sophisticated, using AI and machine learning to create convincing emails, messages, and websites.
-
Increased Targeting of Small and Medium-Sized Businesses: Attackers will increasingly target small and medium-sized businesses, which often have fewer resources to devote to cybersecurity.
-
Growing Use of Social Engineering Tactics: Attackers will continue to use social engineering tactics, such as pretexting and baiting, to trick victims into revealing sensitive information.
-
More Focus on Data Exfiltration: Attackers will increasingly focus on exfiltrating sensitive data, such as financial information and personal identifiable information.
Conclusion
Phishing campaigns are a growing concern for individuals and organizations, and it's essential to stay informed and adapt your security practices to stay ahead of these threats. By following the 7 best practices outlined in this post and staying vigilant, you can significantly reduce the risk of falling victim to phishing attacks. Remember to always be cautious when interacting with emails, messages, or links from unknown sources, and never provide sensitive information without verifying the authenticity of the request.
At LucidTrac, we're committed to helping you stay secure online. If you have any questions or concerns about phishing campaigns or online security, feel free to reach out to us.
Share this Blog Post: https://lcdtrc.link/q081nee
In Case you Missed It - Seach by Tags!

Visit our YouTube channel at https://youtube.com for help and videos about the #LucidTrac Platform.

Introducing the #softwareKing Motivational Mobile App Section: Unleash Your Self Motivational Power
At LucidTrac ERP, we are proud to announce the launch of an exciting new section within our Mobile App: #softwareKing. Designed to inspire, empower, and uplift, #softwareKing brings you an exclusive collection of Daily Motivational Videos, curated to fuel your ambition and drive your success.
With the #softwareKing section, we believe that motivation knows no bounds. That's why we have made these inspirational videos accessible to everyone, without the need for an account or any subscription fees. Simply download our app, and immerse yourself in a world of powerful messages and transformative insights.
Compare LucidTrac to other online platforms
To help you get a better understanding of your needs by comparing LucidTrac to other online ERP / SaaS platforms.
LucidTrac offers a comprehensive solution to streamline all of your business operations.
With its fully customizable features, LucidTrac allows you to tailor the platform to meet the specific needs of your business.

Compare LucidTrac to
Zoho CRM

Compare LucidTrac to
Zendesk CRM

Compare LucidTrac to
Freshdesk CRM

Compare LucidTrac to
Salesforce CRM

Compare LucidTrac to
Monday CRM

Compare LucidTrac to
HubSpot CRM

Compare LucidTrac to
Keap CRM

Compare LucidTrac to
Sugar CRM

Compare LucidTrac to
SherpaDesk CRM
| Comparing Feature | LucidTrac | Zoho CRM | Zendesk CRM | Freshdesk CRM | Salesforce CRM | Monday CRM | HubSpot CRM | Keap CRM | Sugar CRM | SherpaDesk CRM |
| Price | $300 Unlimited Users | $49 Avg/Per User | $149 Avg/Per User | $109 Avg/Per User | $125 Avg/Per User | $99 Avg/Per User | $99 Avg/Per User | $49 Avg/Per User | $45 Avg/Per User | $49 Avg/Per User |
| Free Trial | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Support 24/7 | Yes | Yes | No | No | No | No | No | No | No | No |
| Developer API | Yes | Yes | No | Yes | No | No | No | No | No | Yes |
| Dashboards | Yes | Yes | No | Yes | No | Yes | No | No | Yes | No |
| To-Dos | Yes | Yes | No | Yes | No | Yes | No | No | Yes | Yes |
| Products & Assets | Yes | Yes | No | Yes | No | Yes | No | No | Yes | Yes |
| User Roles | Yes | Yes | No | Yes | No | Yes | No | No | Yes | No |
| 2FA (Two-Factor Authentication) | Yes | Yes | No | Yes | No | Yes | No | No | Yes | No |
| Multi Method Importing | Yes | Yes | No | No | No | Yes | No | No | No | No |
| Documents & Templates | Yes | No | No | No | No | No | No | No | No | No |
| iOS/Android Apps | Yes | Yes | No | No | No | No | No | No | No | Yes |
| Statistics & Reporting | Yes | Yes | No | Yes | No | No | No | No | No | Yes |
| Storage | 500G Base Node | 1G | 1G | 1G | 1G | 1G | 1G | 1G | 1G | - |
| Monthly Payments | Yes | Yes | No | Yes | No | No | No | No | No | Yes |
| Campaigns | Yes | Yes | No | Yes | No | No | No | No | No | No |
| Exporting Services | Yes | Yes | Yes | Yes | No | No | Yes | No | Yes | No |
| Emailing | Yes | Yes | No | Yes | No | No | No | No | No | No |
| SMS Inbound/Outbound | Yes | Yes | No | Yes | No | No | No | No | No | No |
| Voice Calling Inbound/Outbound | Yes | Yes | No | Yes | No | No | No | No | No | No |
| IVR Services | Yes | Yes | No | Yes | No | No | No | No | No | No |
| Google Calendar/Authentication | Yes | Yes | No | Yes | No | No | No | No | No | No |
| Service Tickets / Time Tracking | Yes | Yes | No | Yes | No | No | No | No | No | Yes |
| Email to Service Ticket Services | Yes | Yes | yes | Yes | No | No | No | No | No | Yes |
| Time Clock / Payroll Exporting | Yes | No | No | No | No | No | No | No | No | No |
| Networking / IP & Host Management | Yes | No | No | No | No | No | No | No | No | No |
| Web Forms / Landing Pages | Yes | Yes | No | Yes | No | No | Yes | No | No | No |
| Invoice/Payment Collections Tools | Yes | No | No | No | No | No | No | No | No | No |
| Customized Programming | Yes | No | No | No | No | No | No | No | No | No |

Mr. Kevin Johnson
BlueSpruce Consulting Services, LLC.

Mr. Craig Stonaha
CEO Laughing Rock Technologies, LLC.
John Adams
President/CEO - RDI

Dennis Canlas
USCR
Brian Gomez
Gomez Check Cashing

Mr. Michael Graziano
Prime Time Mortgage Corp.

Mr. Nicholas Tannous
NWT Enterprises Ltd - San Juan, Trinidad and Tobago

Mrs. Cynthia Garrett
Berks ENT - Reading PA