Another Day and yet Another Zero-Day CVE
The constantly evolving digital landscape poses new security threats and vulnerabilities as technology advances. Cyber criminals become more sophisticated and use cutting-edge methods to penetrate systems, and thus it is important for cybersecurity experts to remain updated on these emerging threats. Common Vulnerabilities and Exposures (CVE) is a crucial tool utilized by these professionals to assess and address security risks.
What is a CVE?
Common Vulnerabilities and Exposures (CVE) are a standardized method of identifying and cataloging security vulnerabilities in computer systems. CVE is managed by the nonprofit organization MITRE, who defines CVE as a "dictionary of publicly known information security vulnerabilities and exposures."
The main purpose of CVE is to enable system administrators, developers, and vendors to quickly identify potential security risks and define steps for mitigating them. Each vulnerability or exposure entry on the CVE list has an associated unique identifier that can be used to look up more detailed information about it online. The list also includes references to other resources where users can find even more detailed information.
MITRE continuously updates the list with new entries as they become available, ensuring up-to-date coverage of existing threats.

What is a Zero-Day Vulnerability?
.png)
A zero-day vulnerability, also known as a zero-hour vulnerability, is a security flaw in software or hardware that can be exploited by hackers to gain unauthorized access. These vulnerabilities are serious threats because they can remain undetected for an extended period of time and allow attackers to bypass existing security measures.
Zero-day vulnerabilities occur when developers fail to anticipate all the possible ways a system may be attacked. Attackers look for these weaknesses and exploit them in order to gain access to sensitive information or systems. Once inside, they can install malware, steal data or cause other malicious activities. The most effective way to protect against zero-day vulnerabilities is through regular patching and updating of security solutions such as firewalls and antivirus programs.
What is the Impact of a Zero-Day?

For organizations, the impact of a zero day exploit is extremely significant due to their access to more secure systems including financial data, customer records, intellectual property and other confidential information. If these systems are breached it can result in significant financial losses as well as reputational damage for an organization. In addition, if hackers gain control of critical infrastructure then this could have serious implications for public safety or cause disruption to essential services.
For individuals, zero days can also have damaging effects - from personal data being stolen or malicious code running on their computers without them knowing about it.
Disclosing & Fixing Zero-Days
As technology continues to evolve, cyber threats are becoming increasingly sophisticated. With the rise of zero-day vulnerabilities, organizations must understand the importance of quickly disclosing and fixing these security flaws.
A zero-day vulnerability is an exploit that takes advantage of a system flaw before it has been publicly disclosed or patched by its vendor. Hackers can leverage these vulnerabilities to gain access to sensitive data, cause harm to systems and networks, and even launch ransomware attacks. The only way organizations can mitigate this risk is by promptly identifying, reporting and patching such software vulnerabilities once they’ve been discovered.
Organizations need to develop a comprehensive security strategy that includes constant monitoring for potential threats as well as timely patch deployment when new updates become available. By doing so they can ensure their networks remain secure from malicious actors looking to exploit zero-day vulnerabilities.
Examples of Recent Zero-Day Discoveries
Zero-day discoveries are a key indicator of the ever-evolving security landscape. First identified in the 1970s (The Creeper virus was first detected on ARPANET, the forerunner of the Internet, in the early 1970s.), they refer to vulnerabilities that have yet to be addressed by developers or vendors. As cyber threats become increasingly complex, organizations should remain aware of recent zero-day discoveries as an important part of their overall security strategy.
Recent examples include CVE-2019–14287, a vulnerability found in Linux kernel versions 5 and higher. The exploit allowed attackers access to sensitive data and system files on vulnerable machines, making it a significant security risk for organizations using those operating systems. Another example is CVE-2020–0796, dubbed 'SMBghost' by Microsoft. This vulnerability affects Windows 10 systems and was discovered after malicious actors had already begun exploiting it in the wild.
The Log4j CVE-2021-44228 is a security vulnerability in the Apache software project’s log4j library. It is classified as a Critical severity issue, meaning that any device using the affected version of Log4j could be exposed to malicious attacks.
Log4j is an open-source logging library used in many applications, including web servers and cloud computing systems. The CVE was discovered by researchers at Check Point Research, who found that attackers could exploit the vulnerability to gain access to sensitive data or execute arbitrary code on vulnerable devices. Due to the widespread use of this tool and the criticality of its vulnerability, it is essential for all users of any version prior to 2.13.2 released on June 3rd 2020 to update their versions as soon as possible and ensure their systems are secure.

The Industry Implication
The cybersecurity industry is constantly changing and evolving as new threats emerge. Zero-day and none discovered CVE threats are two of the most common cyberattacks that companies must guard against.
We learned that a zero-day threat is a security vulnerability that is unknown to the public, or even to the company itself, until it has been exploited by a malicious hacker or criminal organization. These types of attacks can be devastating as they occur without warning and can have serious implications for businesses who are unprepared. None discovered CVE threats involve vulnerabilities that have not yet been identified in software, hardware, or networks. These dangers may present themselves in the form of weak passwords or unpatched systems which could potentially put confidential information at risk if left unprotected.
In Conclusion
There are a variety of malicious cyber threats that organizations and individuals must be aware of, including zero-day attacks, phishing scams and known CVEs. These threats have become increasingly sophisticated, making it more difficult to protect yourself from them. To ensure your safety online, it is important to understand the best way to protect yourself from these threats.
To start with, having a robust security system in place is essential for protecting against zero-day or phishing attacks. A comprehensive security solution should include antivirus software as well as firewalls and malware detection programs that detect malicious behavior in real time. Additionally, staying up to date on patches for all applications can also help mitigate any potential vulnerabilities associated with known CVEs.
In addition to implementing a strong security system, you and all users should also be mindful of their online activities and be alert for suspicious emails or websites.
Share this Blog Post: https://lcdtrc.link/4q8ez6g
In Case you Missed It - Seach by Tags!

Visit our YouTube channel at https://youtube.com for help and videos about the #LucidTrac Platform.

Introducing the #softwareKing Motivational Mobile App Section: Unleash Your Self Motivational Power
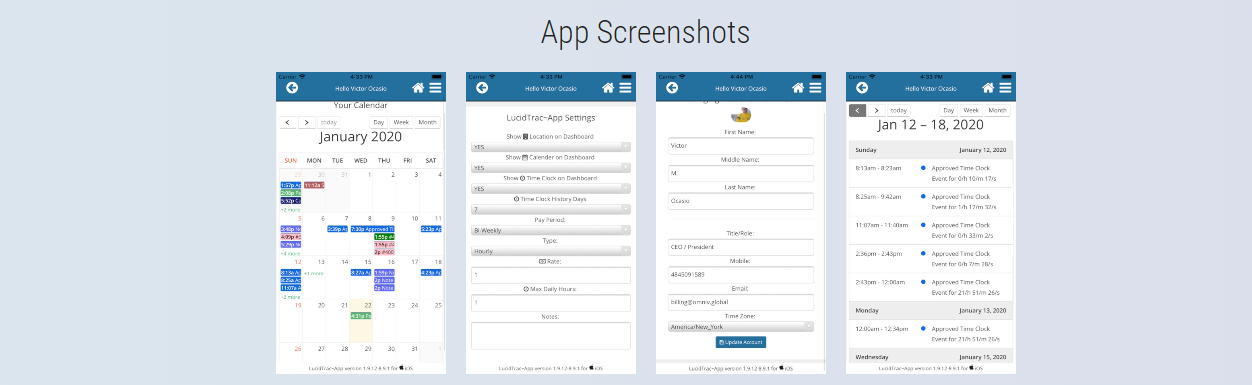
At LucidTrac ERP, we are proud to announce the launch of an exciting new section within our Mobile App: #softwareKing. Designed to inspire, empower, and uplift, #softwareKing brings you an exclusive collection of Daily Motivational Videos, curated to fuel your ambition and drive your success.
With the #softwareKing section, we believe that motivation knows no bounds. That's why we have made these inspirational videos accessible to everyone, without the need for an account or any subscription fees. Simply download our app, and immerse yourself in a world of powerful messages and transformative insights.
Compare LucidTrac to other online platforms
To help you get a better understanding of your needs by comparing LucidTrac to other online ERP / SaaS platforms.
LucidTrac offers a comprehensive solution to streamline all of your business operations.
With its fully customizable features, LucidTrac allows you to tailor the platform to meet the specific needs of your business.

Compare LucidTrac to
Zoho CRM

Compare LucidTrac to
Zendesk CRM

Compare LucidTrac to
Freshdesk CRM

Compare LucidTrac to
Salesforce CRM

Compare LucidTrac to
Monday CRM

Compare LucidTrac to
HubSpot CRM

Compare LucidTrac to
Keap CRM

Compare LucidTrac to
Sugar CRM

Compare LucidTrac to
SherpaDesk CRM
| Comparing Feature | LucidTrac | Zoho CRM | Zendesk CRM | Freshdesk CRM | Salesforce CRM | Monday CRM | HubSpot CRM | Keap CRM | Sugar CRM | SherpaDesk CRM |
| Price | $300 Unlimited Users | $49 Avg/Per User | $149 Avg/Per User | $109 Avg/Per User | $125 Avg/Per User | $99 Avg/Per User | $99 Avg/Per User | $49 Avg/Per User | $45 Avg/Per User | $49 Avg/Per User |
| Free Trial | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Support 24/7 | Yes | Yes | No | No | No | No | No | No | No | No |
| Developer API | Yes | Yes | No | Yes | No | No | No | No | No | Yes |
| Dashboards | Yes | Yes | No | Yes | No | Yes | No | No | Yes | No |
| To-Dos | Yes | Yes | No | Yes | No | Yes | No | No | Yes | Yes |
| Products & Assets | Yes | Yes | No | Yes | No | Yes | No | No | Yes | Yes |
| User Roles | Yes | Yes | No | Yes | No | Yes | No | No | Yes | No |
| 2FA (Two-Factor Authentication) | Yes | Yes | No | Yes | No | Yes | No | No | Yes | No |
| Multi Method Importing | Yes | Yes | No | No | No | Yes | No | No | No | No |
| Documents & Templates | Yes | No | No | No | No | No | No | No | No | No |
| iOS/Android Apps | Yes | Yes | No | No | No | No | No | No | No | Yes |
| Statistics & Reporting | Yes | Yes | No | Yes | No | No | No | No | No | Yes |
| Storage | 500G Base Node | 1G | 1G | 1G | 1G | 1G | 1G | 1G | 1G | - |
| Monthly Payments | Yes | Yes | No | Yes | No | No | No | No | No | Yes |
| Campaigns | Yes | Yes | No | Yes | No | No | No | No | No | No |
| Exporting Services | Yes | Yes | Yes | Yes | No | No | Yes | No | Yes | No |
| Emailing | Yes | Yes | No | Yes | No | No | No | No | No | No |
| SMS Inbound/Outbound | Yes | Yes | No | Yes | No | No | No | No | No | No |
| Voice Calling Inbound/Outbound | Yes | Yes | No | Yes | No | No | No | No | No | No |
| IVR Services | Yes | Yes | No | Yes | No | No | No | No | No | No |
| Google Calendar/Authentication | Yes | Yes | No | Yes | No | No | No | No | No | No |
| Service Tickets / Time Tracking | Yes | Yes | No | Yes | No | No | No | No | No | Yes |
| Email to Service Ticket Services | Yes | Yes | yes | Yes | No | No | No | No | No | Yes |
| Time Clock / Payroll Exporting | Yes | No | No | No | No | No | No | No | No | No |
| Networking / IP & Host Management | Yes | No | No | No | No | No | No | No | No | No |
| Web Forms / Landing Pages | Yes | Yes | No | Yes | No | No | Yes | No | No | No |
| Invoice/Payment Collections Tools | Yes | No | No | No | No | No | No | No | No | No |
| Customized Programming | Yes | No | No | No | No | No | No | No | No | No |

Mr. Kevin Johnson
BlueSpruce Consulting Services, LLC.

Mr. Craig Stonaha
CEO Laughing Rock Technologies, LLC.
John Adams
President/CEO - RDI

Dennis Canlas
USCR
Brian Gomez
Gomez Check Cashing

Mr. Michael Graziano
Prime Time Mortgage Corp.

Mr. Nicholas Tannous
NWT Enterprises Ltd - San Juan, Trinidad and Tobago

Mrs. Cynthia Garrett
Berks ENT - Reading PA