Understanding the XZ Utils Supply Chain Attack: A High School Level Explanation
Hey, everyone! Today, we're diving into a story that sounds like it's straight out of a spy novel, but it's real and it happened in the tech world around March 29th 2024. It's about the XZ Utils Supply Chain Attack. If you're wondering what that is, don't worry, we'll break it down into bits and pieces that are easy to digest, just like how you'd eat a giant burger. Let's get into it!
What Happened?
In the world of computers and the internet, there's something called XZ Utils. Think of XZ Utils like a magical tool that can make big files smaller, so they're easier to share and store. It's super important because it's used by lots of different software, including the big systems that run on many computers (Linux distributions, to be specific).
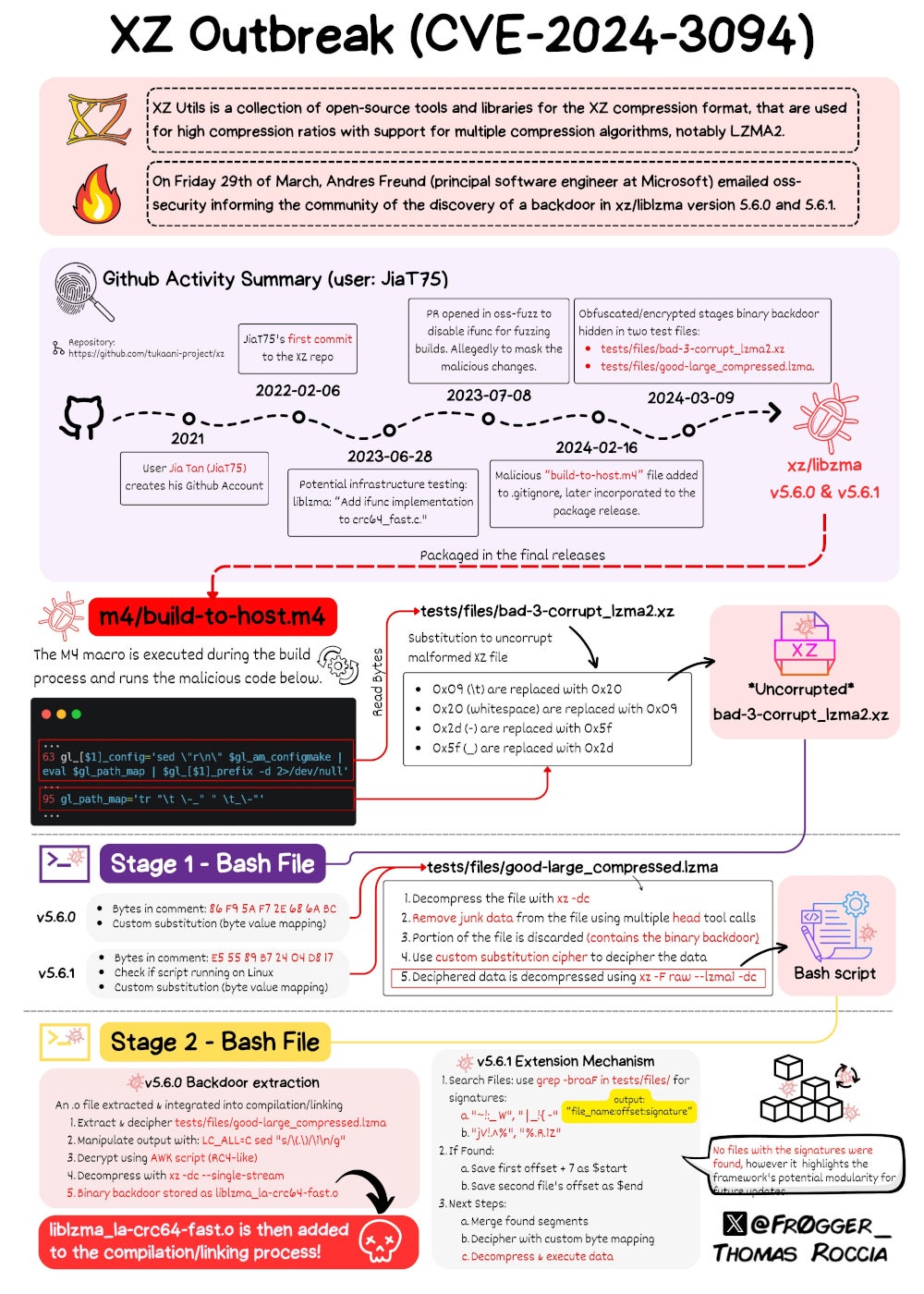
But here's the plot twist: a bad actor (and no, we're not talking about someone who can't act in movies) named Jia Tan, sneaked into the XZ Utils project. Over time, they gained the trust of the community and became a maintainer of the project. Then, they did something sneaky: they introduced a backdoor in versions 5.6.0 and 5.6.1 of XZ Utils. This backdoor is like leaving a secret path open for thieves to get into your house without you knowing.
The Discovery
On March 29, 2024, Microsoft software engineer Andres Freund reported the discovery of the backdoor. The discovery of the CVE-2024-3094 backdoor within XZ Utils posed a significant security risk, particularly affecting the SSHD protocol, a component of the OpenSSH server software responsible for managing SSH connections. This vulnerability allowed for remote code execution through an SSH login certificate, impacting only the 5.6.0 and 5.6.1 versions of XZ Utils.
Why Should We Care?
You might be thinking, "Okay, cool story, but why should I care?" Well, if this backdoor had gone unnoticed for longer, it could have let bad guys sneak into a lot of important places on the internet, putting lots of data and personal information at risk. It's a big deal because it shows how something small can affect a lot of people and systems.
Which operating systems are impacted by the XZ backdoor?
Thanks to Freund’s accidental discovery, the attack was stopped before being spread on a wider scale. The cybersecurity company Tenable exposed the following operating systems known to be affected by the XZ backdoor:
- Fedora Rawhide.
- Fedora 40 Beta.
- Fedora 41.
- Debian testing, unstable and experimental distributions versions 5.5.1alpha-01 to 5.6.1-1.
- openSUSE Tumbleweed.
- openSUSE MicroOS.
- Kali Linux.
- Arch Linux.
How Did They Do It?
The attacker didn't just walk in and plant the backdoor. They were sneaky about it. They made small changes over time that seemed harmless at first but were actually part of a bigger, malicious plan. This plan involved making the backdoor work only under certain conditions, making it harder to spot.
What's Being Done?
After the discovery, the good guys (like security researchers and the open-source community) jumped into action. They came up with ways to find out if a system has the bad version of XZ Utils and how to fix it if it does. They advised everyone to use a safe version of XZ Utils (5.4.6 is the hero version here) and shared tools to help check systems for the sneaky backdoor.
How Can You Check If Your System Is Vulnerable?
Now, for the DIY part: how can you check if your computer is caught in this web? There are a few steps you can take:
-
Use Detection Tools: There are free tools available that can scan your system to see if it has the vulnerable versions of XZ Utils. One is called XZBackdoor Scanner, and it's like a detective tool that checks for any signs of the backdoor.
-
Check Your Version: If you're comfortable using command lines (think of it as typing special commands that computers understand), you can check the version of XZ Utils on your system. If it's version 5.6.0 or 5.6.1, you'll want to update to a safer version.
-
Stay Updated: Keep your software up to date. When security experts find problems like this, they quickly work to fix them. By updating, you're closing the door on those secret paths the bad guys want to use.
Wrapping Up
So there you have it—a story of how a sneaky backdoor almost caused a lot of trouble, how it was discovered, and what's being done to fix it. It's a reminder that in the digital world, just like in real life, we have to stay vigilant and keep our doors locked to strangers. And by working together and using the right tools, we can keep our digital neighborhood safe.
Remember, knowledge is power, especially when it comes to protecting yourself online. So, stay curious, ask questions, and don't forget to keep your software up to date!
Sources & Citations
- SecurityWeek: "Supply Chain Attack: Major Linux Distributions Impacted by XZ Utils Backdoor" - SecurityWeek
- Microsoft Community Hub: "Microsoft FAQ and guidance for XZ Utils backdoor" - Microsoft Tech Community
- Checkmarx: "Backdoor Discovered in xz" - Checkmarx
- Bitdefender: "Technical Advisory: XZ Upstream Supply Chain Attack" - Bitdefender
Share this Blog Post: https://lcdtrc.link/n7mjpr0
In Case you Missed It - Seach by Tags!

Visit our YouTube channel at https://youtube.com for help and videos about the #LucidTrac Platform.

Introducing the #softwareKing Motivational Mobile App Section: Unleash Your Self Motivational Power
At LucidTrac ERP, we are proud to announce the launch of an exciting new section within our Mobile App: #softwareKing. Designed to inspire, empower, and uplift, #softwareKing brings you an exclusive collection of Daily Motivational Videos, curated to fuel your ambition and drive your success.
With the #softwareKing section, we believe that motivation knows no bounds. That's why we have made these inspirational videos accessible to everyone, without the need for an account or any subscription fees. Simply download our app, and immerse yourself in a world of powerful messages and transformative insights.
Compare LucidTrac to other online platforms
To help you get a better understanding of your needs by comparing LucidTrac to other online ERP / SaaS platforms.
LucidTrac offers a comprehensive solution to streamline all of your business operations.
With its fully customizable features, LucidTrac allows you to tailor the platform to meet the specific needs of your business.

Compare LucidTrac to
Zoho CRM

Compare LucidTrac to
Zendesk CRM

Compare LucidTrac to
Freshdesk CRM

Compare LucidTrac to
Salesforce CRM

Compare LucidTrac to
Monday CRM

Compare LucidTrac to
HubSpot CRM

Compare LucidTrac to
Keap CRM

Compare LucidTrac to
Sugar CRM

Compare LucidTrac to
SherpaDesk CRM
| Comparing Feature | LucidTrac | Zoho CRM | Zendesk CRM | Freshdesk CRM | Salesforce CRM | Monday CRM | HubSpot CRM | Keap CRM | Sugar CRM | SherpaDesk CRM |
| Price | $300 Unlimited Users | $49 Avg/Per User | $149 Avg/Per User | $109 Avg/Per User | $125 Avg/Per User | $99 Avg/Per User | $99 Avg/Per User | $49 Avg/Per User | $45 Avg/Per User | $49 Avg/Per User |
| Free Trial | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Support 24/7 | Yes | Yes | No | No | No | No | No | No | No | No |
| Developer API | Yes | Yes | No | Yes | No | No | No | No | No | Yes |
| Dashboards | Yes | Yes | No | Yes | No | Yes | No | No | Yes | No |
| To-Dos | Yes | Yes | No | Yes | No | Yes | No | No | Yes | Yes |
| Products & Assets | Yes | Yes | No | Yes | No | Yes | No | No | Yes | Yes |
| User Roles | Yes | Yes | No | Yes | No | Yes | No | No | Yes | No |
| 2FA (Two-Factor Authentication) | Yes | Yes | No | Yes | No | Yes | No | No | Yes | No |
| Multi Method Importing | Yes | Yes | No | No | No | Yes | No | No | No | No |
| Documents & Templates | Yes | No | No | No | No | No | No | No | No | No |
| iOS/Android Apps | Yes | Yes | No | No | No | No | No | No | No | Yes |
| Statistics & Reporting | Yes | Yes | No | Yes | No | No | No | No | No | Yes |
| Storage | 500G Base Node | 1G | 1G | 1G | 1G | 1G | 1G | 1G | 1G | - |
| Monthly Payments | Yes | Yes | No | Yes | No | No | No | No | No | Yes |
| Campaigns | Yes | Yes | No | Yes | No | No | No | No | No | No |
| Exporting Services | Yes | Yes | Yes | Yes | No | No | Yes | No | Yes | No |
| Emailing | Yes | Yes | No | Yes | No | No | No | No | No | No |
| SMS Inbound/Outbound | Yes | Yes | No | Yes | No | No | No | No | No | No |
| Voice Calling Inbound/Outbound | Yes | Yes | No | Yes | No | No | No | No | No | No |
| IVR Services | Yes | Yes | No | Yes | No | No | No | No | No | No |
| Google Calendar/Authentication | Yes | Yes | No | Yes | No | No | No | No | No | No |
| Service Tickets / Time Tracking | Yes | Yes | No | Yes | No | No | No | No | No | Yes |
| Email to Service Ticket Services | Yes | Yes | yes | Yes | No | No | No | No | No | Yes |
| Time Clock / Payroll Exporting | Yes | No | No | No | No | No | No | No | No | No |
| Networking / IP & Host Management | Yes | No | No | No | No | No | No | No | No | No |
| Web Forms / Landing Pages | Yes | Yes | No | Yes | No | No | Yes | No | No | No |
| Invoice/Payment Collections Tools | Yes | No | No | No | No | No | No | No | No | No |
| Customized Programming | Yes | No | No | No | No | No | No | No | No | No |

Mr. Kevin Johnson
BlueSpruce Consulting Services, LLC.

Mr. Craig Stonaha
CEO Laughing Rock Technologies, LLC.
John Adams
President/CEO - RDI

Dennis Canlas
USCR
Brian Gomez
Gomez Check Cashing

Mr. Michael Graziano
Prime Time Mortgage Corp.

Mr. Nicholas Tannous
NWT Enterprises Ltd - San Juan, Trinidad and Tobago

Mrs. Cynthia Garrett
Berks ENT - Reading PA